Table Of Content

In reality, we only need the problem title, id, level, and maybe a tags or category field but no need to return the entire problem statement or code stubs here. How you short hand this is not important so long as you are clear with your interviewer. Starting with viewing a list of problems, we'll have a simple GET endpoint that returns a list. I've added some basic pagination as well since we have far more problems than should be returned in a single request or rendered on a single page.
Serviceability or Manageability
A lot of NoSQL technologies also distribute data across servers automatically. A document store is centered around documents (XML, JSON, binary, etc), where a document stores all information for a given object. Document stores provide APIs or a query language to query based on the internal structure of the document itself. Note, many key-value stores include features for working with a value's metadata, blurring the lines between these two storage types. Separating out the web layer from the application layer (also known as platform layer) allows you to scale and configure both layers independently. Adding a new API results in adding application servers without necessarily adding additional web servers.
Ready to ace your next tech interview?
A key-value store generally allows for O(1) reads and writes and is often backed by memory or SSD. Data stores can maintain keys in lexicographic order, allowing efficient retrieval of key ranges. Similar to the advantages of federation, sharding results in less read and write traffic, less replication, and more cache hits.
Disadvantage(s): load balancer
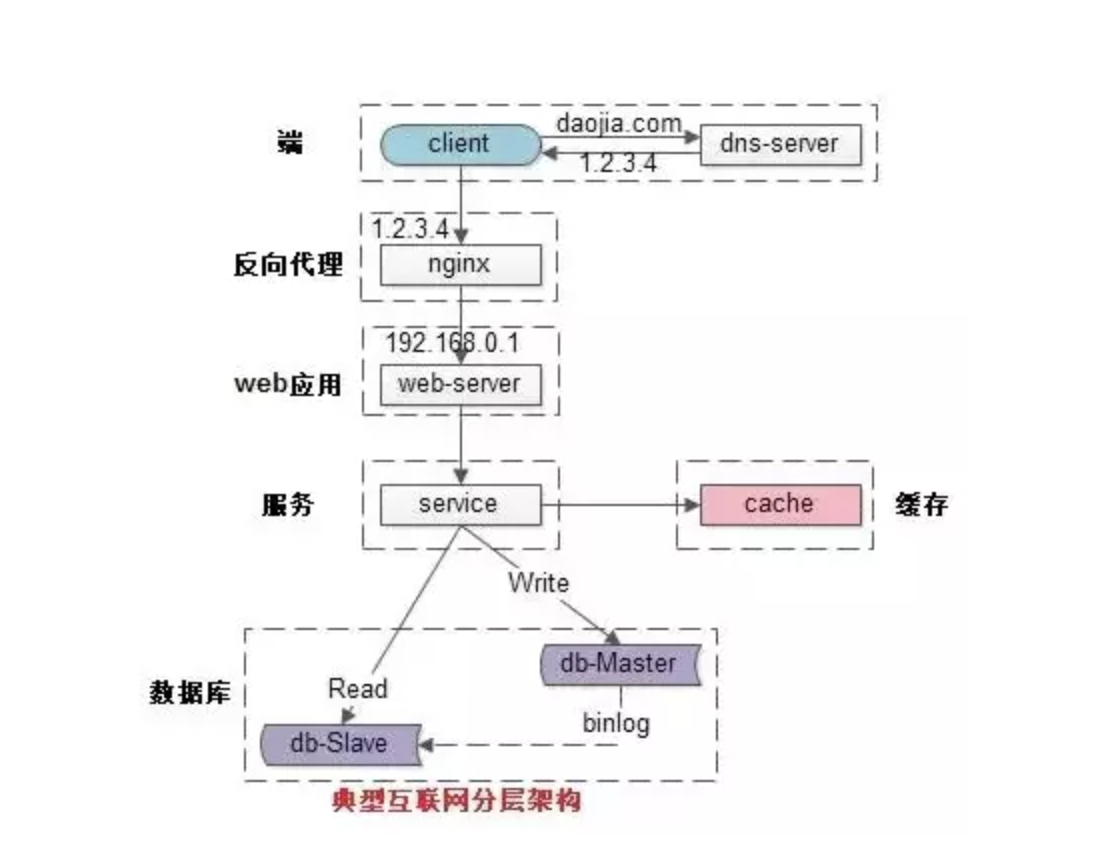
Clients connect to proxy servers to request for a service like a web page, file, connection, etc. Another advantage of a proxy server is that its cache can serve a lot of requests. If multiple clients access a particular resource, the proxy server can cache it and serve it to all the clients without going to the remote server. Placing a cache directly on a request layer node enables the local storage of response data.
How will the system support isolation and security when running user code?
Denormalization attempts to improve read performance at the expense of some write performance. Redundant copies of the data are written in multiple tables to avoid expensive joins. Some RDBMS such as PostgreSQL and Oracle support materialized views which handle the work of storing redundant information and keeping redundant copies consistent. At the cost of flexibility, layer 4 load balancing requires less time and computing resources than Layer 7, although the performance impact can be minimal on modern commodity hardware.
Reliability
By using containerization technology like Docker, isolated execution environments can be created for running user code. Each user's code runs within its own container, separate from the host system, providing a sandboxed environment. Techniques such as resource limitations, network isolation, file system restrictions, timeouts, and execution limits help enforce security within the containers. This would scale independently and is orchestrated like a task queue. NoSQL is a collection of data items represented in a key-value store, document store, wide column store, or a graph database.
High Level Differences Between SQL and NoSQL
Graph databases are optimized to represent complex relationships with many foreign keys or many-to-many relationships. In active-active, both servers are managing traffic, spreading the load between them. Common object-oriented design interview questions with sample discussions, code, and diagrams.
Load balancer vs reverse proxy
The LB sits between the client and the server accepting incoming network, application traffic, and distributing the traffic across multiple backend servers using various algorithms. The complexity of operations supported by distributed data structures can be characterized as a function of these cost units. Keep in mind that factors like "number of messages" are over simplistic because it ignores many factors like network topology, network load, etc. However it is difficult to develop a cost model accounting all these factors, so we proceed with rough estimates of the system behavior. However, if it is available it does not necessarily mean it is reliable.
A Look at the Top Questions for a System Design Interview at Facebook - hackernoon.com
A Look at the Top Questions for a System Design Interview at Facebook.
Posted: Tue, 05 Jan 2021 08:00:00 GMT [source]
Session IDs can be assigned to each user's virtual machine instance, allowing individual sessions to be tracked and managed. This ensures that users can easily resume their work, access their code, and retain their session state, even if they navigate away from the platform. This is a variation of the traditional polling technique that allows the server to push information to a client whenever the data is available. With Long-Polling, the client requests information from the server exactly as in normal polling, but with the expectation that the server may not respond immediately.
Overall, a system's performance will degrade, even if it was designed to scale, with the system size due to management and environment cost. I.e network speed will be slower because machines tend to be far apart from each other, some tasks might not be distributed due to a flaw in the design. At some point these tasks will limit the speed up obtained by the architecture. Ideally, a scalable architecture avoids this situation and attempts to balance the workload on all participating nodes.
Some of them will be shifted to D, while other keys will not be touched. Most of the NoSQL solutions sacrifice ACID compliance for performance and scalability. There are a variety of load balancing methods, which use different algorithms for different needs. A Load Balancer considers two factors before forwarding a request to a backend server.
For example, if you are on a phone call and lose reception for a few seconds, when you regain connection you do not hear what was spoken during connection loss. In the realm of system design, databases and storage systems are the treasure chests that hold the valuable data your system will process. They are the foundations upon which your system will be built, and understanding them is crucial.
Reliability represents one of the main characteristics of any distributed system because any failing machine can be replaced by another healthy one, ensuring the completion of the requested task. For example, lets consider a simple question that asks the maximum depth of a binary tree. Using Python as our example, we can see that the function itself takes in a TreeNode object.
No comments:
Post a Comment